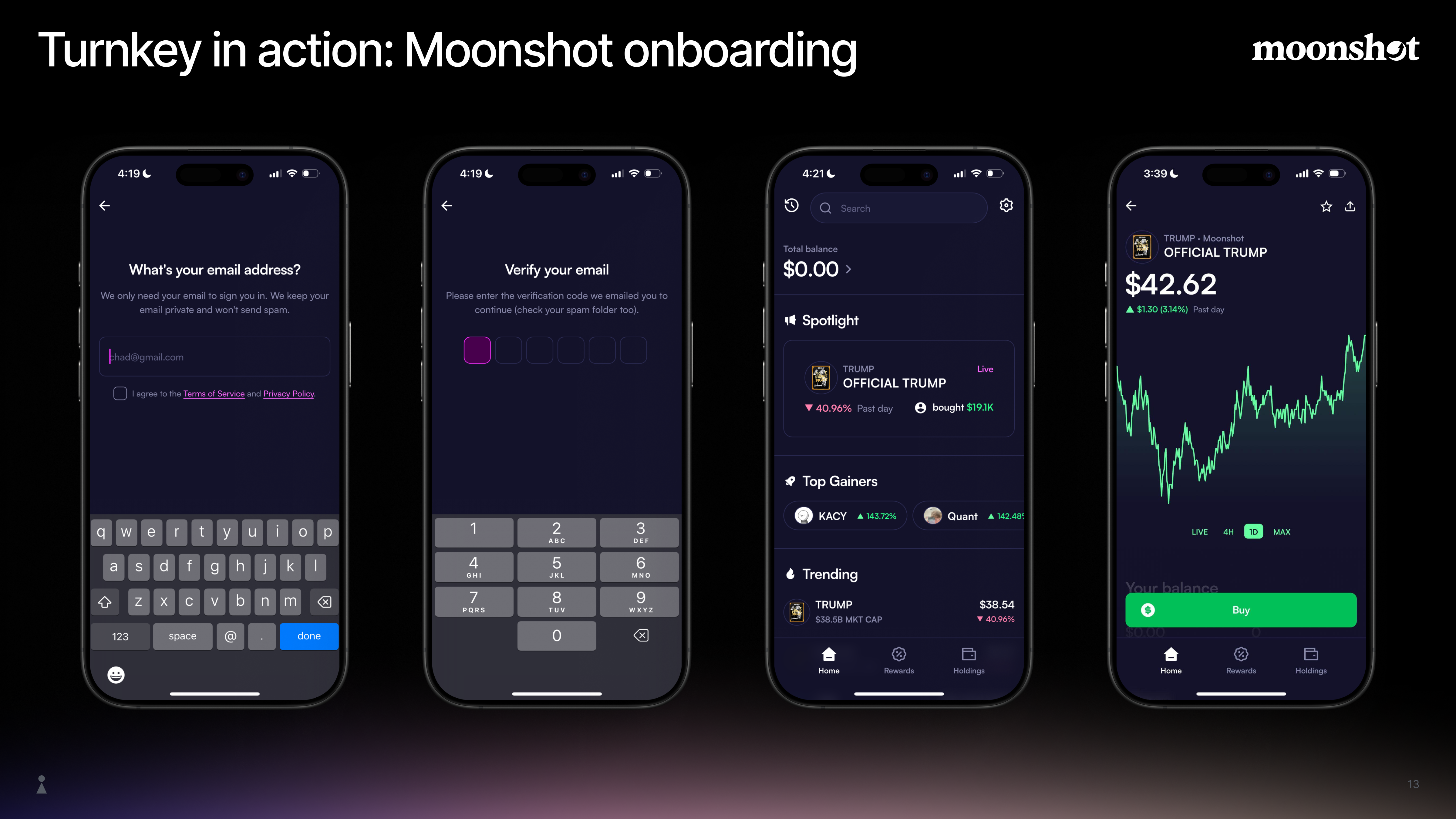
Turnkey delivers a secure, flexible solution for embedding end-user wallets directly into your application. Users sign in with familiar methods (passkeys, email, OAuth), without seed phrases, browser extensions, or external wallets. Turnkey lets you compose your app’s core experiences (onboarding, wallet flows, and transactions) with full control, without restricting critical product decisions to pre-built flows. Keys stay inside hardware-backed Trusted Execution Environments (TEEs), ensuring private keys are never exposed to your developers or to Turnkey. You can use the Embedded Wallet Kit for fast integration, or Turnkey SDKs and the API for more customization. Leading apps like Moonshot, Infinex, and Axiom use Turnkey for embedded consumer wallets in production.
Key implementation decisions
Turnkey enables developers to tailor non-custodial, embedded user wallets across dimensions such as custody model, authentication, and more. See the key implementation decisions below to curate the exact user experience you need. For a full map of embedded wallet capabilities, see the Features overview.| Decision | Explanation | Learn more |
|---|---|---|
| Custody model | Determine the appropriate custody model for your app. Options include user-controlled, app-controlled, or delegated/hybrid. Configure via policies and sub-organization settings. | Delegated Access, Sub-Organization Customization |
| Authentication methods | Choose user auth methods: Passkeys, OAuth/email, or SMS. You can use the Auth Proxy for backend-signed OTP/OAuth/signup without your own backend, or wire auth to your app. | Authentication Overview, Auth Proxy |
| Session management | Allow a user to take multiple, contiguous actions in a defined period of time. Actions include: Read-write or read-only. | Sessions |
| Wallet architecture | Choose between key-based (HD) or smart contract wallets for your users. Turnkey supports both. | Wallets Concept, Transaction Management |
| Gas sponsorship | Integrate a gasless UX via sponsored transactions to cover who pays gas and how transactions are broadcast. | Transaction Management, Sending sponsored transactions |
| Key portability | Determine whether users can import or export keys. | Import/Export |
Custody model
Choose how much control users and your app have over signing:| Model | Description | Why choose this? |
|---|---|---|
| User-controlled | Only the user can authorize actions (self-custody). | Full Sovereignty: Best for non-custodial apps where users require exclusive signing authority via their own authenticators (e.g., passkeys). |
| App-controlled | Your backend can authorize actions (automation, trading, subscriptions). | Seamless Automation: Ideal for custodial products like trading bots or subscriptions that require acting on a user’s behalf without manual approval. |
| Delegated / hybrid | Scoped permissions shared between user and backend. | Frictionless UX: Enables background actions (e.g., gas sponsorship or scheduled ops) while keeping the user in final control of asset transfers. |
Authentication
Balance security and friction for your audience:- Passkeys: Phishing-resistant, biometric. See passkey authentication.
- OAuth / email: Familiar, low-friction. See Authentication Overview.
- SMS: Market-dependent; consider risk and compliance.
Session management
Choose how users stay authorized and where session credentials live:- Read-write vs read-only: Read-write sessions (OTP, OAuth, passkey sessions) let users perform multiple signed actions in a time window. Read-only sessions suit low-touch apps where you mainly need to read data (e.g., via parent-org access or a read-only session token).
- Storage: IndexedDB (web) for persistent, client-held sessions without exposing keys to your JavaScript; SecureStorage (mobile); or LocalStorage (keys in app-accessible storage).
- Session duration: Default: 15 minutes (configurable via
expirationSeconds).
Wallet architecture
Choose where keys are generated and how wallets interact with the blockchain.| Approach | Pros | Considerations |
|---|---|---|
| Key-based (HD wallets) | Chain-agnostic, no on-chain deployment, broad compatibility. | Standard derivation and signing. |
| Smart contract wallets | Gas sponsorship, batching, advanced permissions. | Requires on-chain deployment and infrastructure. |
Gas sponsorship
Provide gasless UX by sponsoring gas for your users. Turnkey supports sponsored transactions and relay integration so users can sign and send without holding native tokens. See Transaction Management for gas sponsorship, transaction construction, broadcast, nonce management and monitoring capabilities.Key portability
Enable key portability and define whether users can import or export private keys. Enabling export can support user sovereignty and long-term trust. See Import/Export wallets.Core security principles
Embedded consumer wallet with Turnkey is built on these key principles:- Keys never leave the enclave: Private keys live in Trusted Execution Environments (TEEs). All derivation and signing happen inside verifiable infrastructure; only signatures are returned. Remote attestation lets you verify enclave integrity. Raw keys are never exposed to your app or to Turnkey.
- Authenticator-bound requests: Every sensitive operation is signed by a user-held authenticator (passkey, email, etc.). The enclave verifies the signature and then performs the operation. No request, no signing; a compromise outside the enclave cannot move funds. See Authentication Overview for supported methods and Enclave to end-user secure channel for how requests are verified.
- Scoped, programmable control: Choose non-custodial, hybrid, or app-controlled custody. Policies and sub-organization isolation limit who can sign what.
- Trusted vs. untrusted separation: Verification and execution run only inside secure enclaves. Trusted and untrusted infrastructure are strictly separated so that a breach of your app or backend does not expose keys or signing capability.
Architecture at a glance
User authentication flows into a signed request to Turnkey. Inside the enclave, the policy engine evaluates the request; key derivation and signing follow, and only the signature is returned. Your app can then broadcast the transaction through another provider or with Turnkey Transaction Management. For data flow and infrastructure details, see Embedded Wallets overview and Secure enclaves.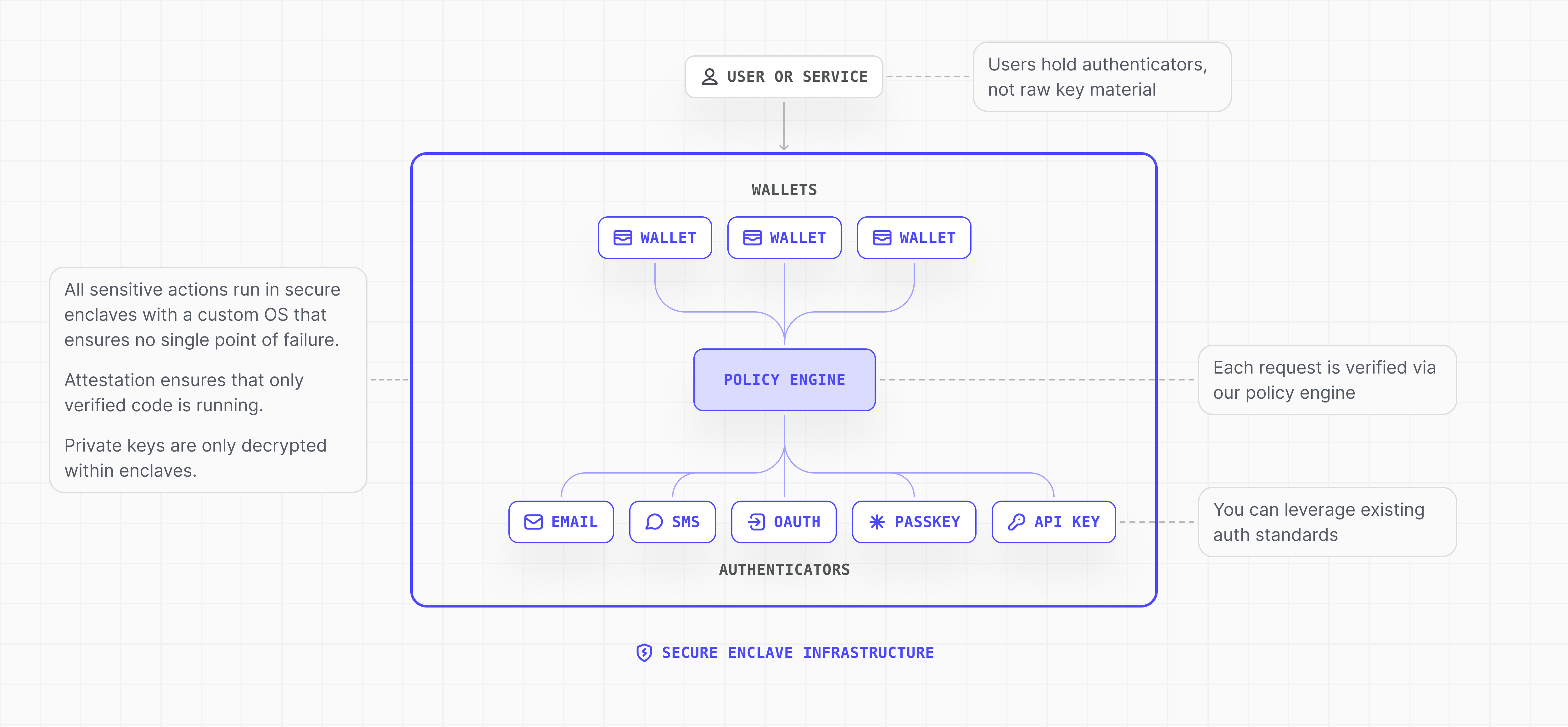
Example: Neobank-style embedded consumer wallet
Typical requirements and how Turnkey addresses them:| Requirement | Turnkey capability |
|---|---|
| Seamless onboarding | Automated provisioning via Quickstart and SDKs |
| User custody without key exposure | Keys remain in secure enclaves; only signatures are returned |
| Gasless UX | Sponsored transactions and sending sponsored transactions |
| Email-based auth and recovery | Sub-organization recovery |
| Send without wallet setup | Claim links: send via URL; recipient claims with email |
| Backend automation | Delegated access and scoped signing policies |
| Multichain support | Chain-agnostic derivation and signing; Networks and Wallets Concept |
| Fast integration | Code Examples Hub and SDKs |
Setting up your embedded consumer wallet
Follow these steps to launch an embedded consumer wallet experience inside your app.Create a Turnkey Org & Configure Authentication
Create an organization in the Turnkey Dashboard and choose how end users authenticate (Email OTP, Passkeys, OAuth).Docs
Add Turnkey to Your Client App
Install and initialize the Turnkey SDK at app startup so sessions and wallet operations are ready immediately.Docs
Implement Login, Signup & Session Handling
Build your login/signup flow and gate wallet actions until:
- The user is authenticated
- The Turnkey client is initialized
Create a Sub-Organization & Wallet Per User
On first login:
- Create a sub-organization
- Create a wallet
- Create required accounts (e.g., Ethereum, Solana)
Enable Core Wallet Actions in the UI
Expose wallet functionality directly inside your app.Signing DocsImport / Export / Recovery (Optional) Docs
Next steps
Ready to build? You can start with the Embedded Wallets Quickstart, explore the Features overview, or browse the Code Examples Hub.