What Is an Agentic Wallet?
An agentic wallet is a crypto wallet that an AI agent or automated backend can operate programmatically—signing transactions, interacting with smart contracts, and executing onchain strategies without requiring human approval for every action. This enables a new class of onchain applications:- Autonomous trading bots
- DeFi yield optimizers
- AI portfolio managers
- Automated payment processors
- Multi-agent coordination systems
Why Build on Turnkey
- Private keys never leave the secure enclave - Unlike solutions that expose raw keys, Turnkey generates and stores keys in hardware-backed secure enclaves. Your agent authenticates via an API key and receives signatures—it never touches the private key itself.
- Sub-100ms signing latency - Signing speeds 100x faster than MPC-based alternatives, enabling agents to react to market movements and onchain events in real time. Transaction Management automates construction, gas sponsorship, and broadcasting.
- Granular policy engine - Every signing request is evaluated by Turnkey’s Policy Engine inside the secure enclave before a signature is produced. Scope exactly what the agent can sign by recipient address, contract address, function selector, chain ID, and transaction value limits.
- Multi-chain support - One integration covers EVM chains, Solana, Bitcoin, Tron, and any blockchain using supported cryptographic curves.
- Consensus for high-stakes actions - For sensitive operations, require both the agent and a human (or another agent) to approve a transaction before it executes. Provides defense-in-depth even if the agent behaves unexpectedly.
- Framework agnostic - Low-level cryptographic primitives without imposing opinions on your agent architecture. Integrates naturally with LangChain, CrewAI, Vercel AI SDK, and agentic protocols like x402 and OpenClawd.
Architecture
The diagram below shows how an AI agent gets scoped access through Delegated Access: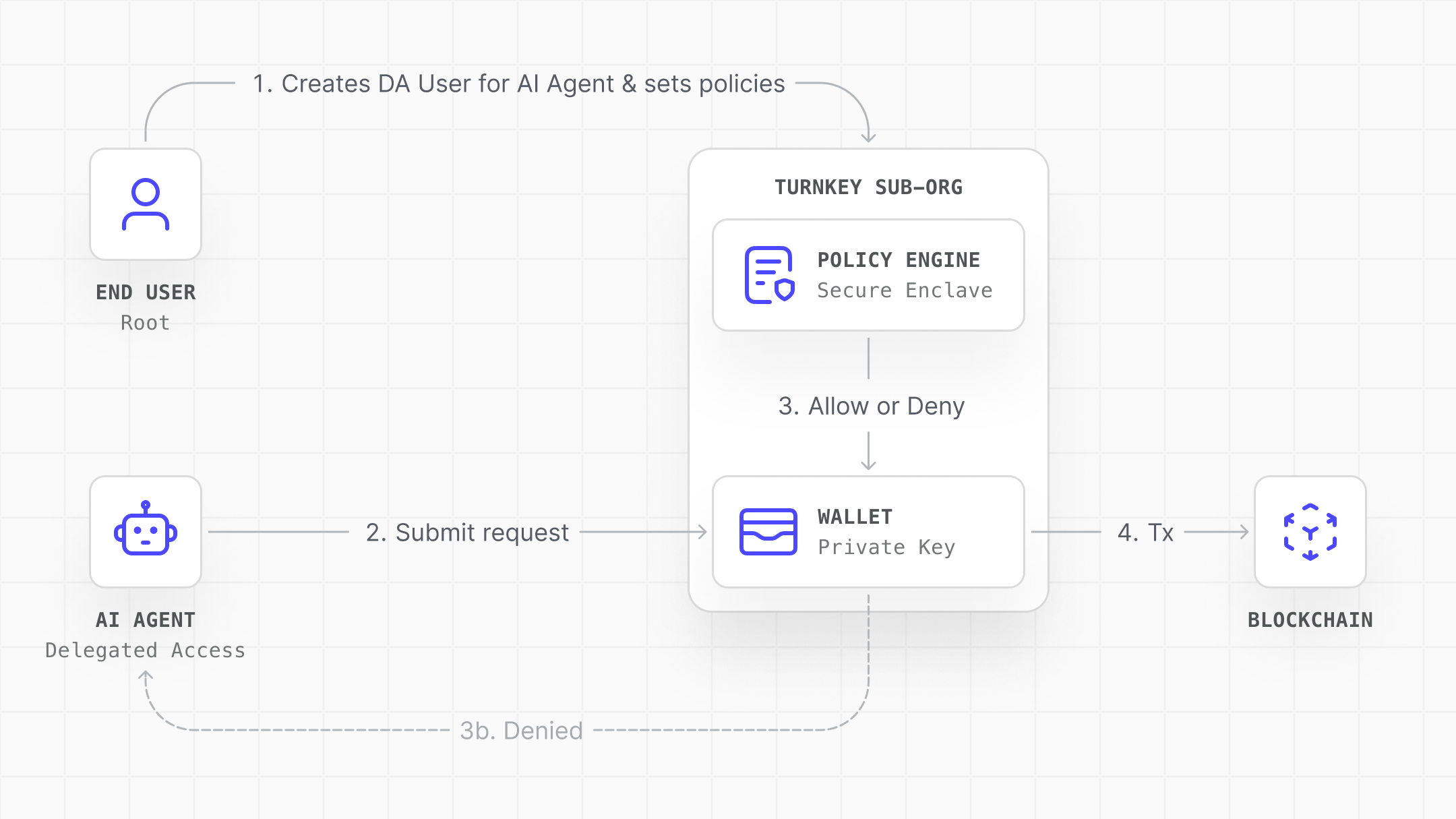
- Setup: The end user (root) creates a Delegated Access user and policies
- Request: The AI agent sends signing requests using its P-256 API key
- Evaluation: The Policy Engine evaluates the request inside the secure enclave
- Execution: If approved, the wallet signs and the transaction is broadcast. If denied, it’s rejected before a signature is produced.
Three Critical Properties
- Separation of control: The end user owns the wallet and sets the rules. The agent operates within those rules.
- Zero key exposure: The agent never touches the private key. It receives signatures, not keys.
- Cryptographic enforcement: Policies are evaluated in the secure enclave—no way to bypass them from application code.