Why Turnkey for Smart Contract Management?
Turnkey provides a highly secure, predictable, and flexible solution for managing onchain assets. Our approach combines mature, cryptographic security with Role-Based Access Control (RBAC) to implement least privilege access and programmatically sign critical smart contract operations, such as minting, burning, and pausing.Core security principles
Turnkey’s solution is engineered to meet the operational and security needs of high-value, high-scrutiny contracts:- Zero exposure of private keys: Private and signing keys are default generated and kept within Turnkey’s secure enclave, never directly exposed or handled by users or automated systems.
- Strict access control (RBAC): Every action – from deployment to token minting to upgrades – is explicitly permissioned via Policies. If a user or automated system is not explicitly allowed to perform an action, they cannot.
- Predictable and flexible workflows: Policies allow for granular control over permissions based on transaction type, chain ID, contract address, function hash, and even transaction values. This flexibility allows businesses to meet both automated and human-operator review requirements.
- Enhanced operational security: Workflows ensure that all contract deployments and actions come from known, authorized addresses, adding a layer of transparency and accountability to all onchain activity.
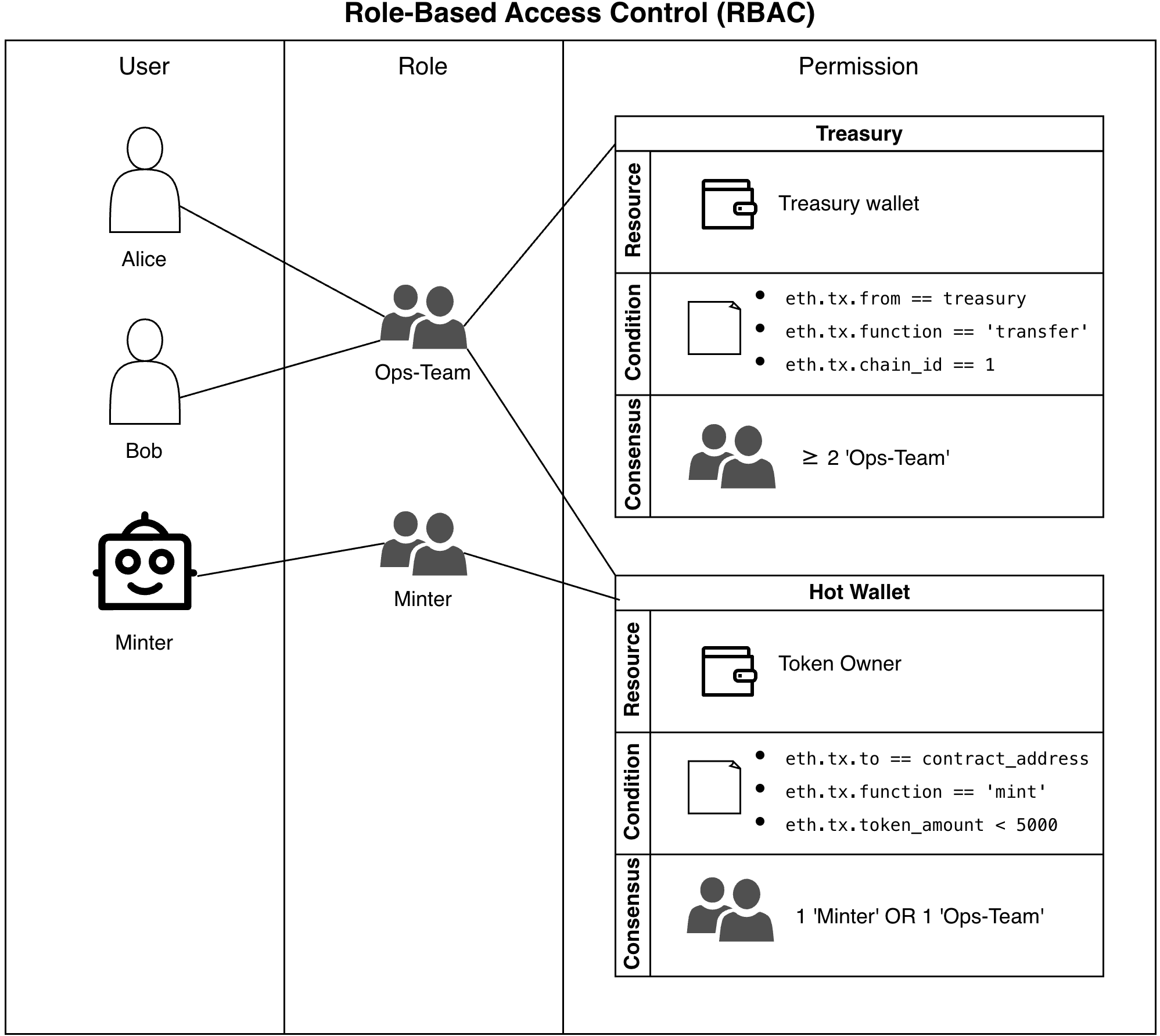
A high-stakes example: Stablecoins and RWAs
Consider the management of Stablecoins or tokenized Real-World Assets, which often secure billions of dollars in value. These high-value contracts require workflows that demand absolute control and accountability. Typical needs for high-value contracts:| Need | Solution |
|---|---|
| All actions must come from known addresses | Wallets are created and controlled within a Turnkey organization |
| Access must be strictly permissioned | Policies enforce RBAC and least-privilege for all signing actions |
| Keys must never be exposed | Keys remain secure in secure enclave; only signatures are provided |
| Must support automation and human review | Policies can be written to allow automation for common tasks, or require multi-party consensus for sensitive ones |
How Turnkey secures the lifecycle
Turnkey provides secure, granular control across the entire contract lifecycle:Secure organization setup
The first step involves creating a Turnkey Organization and populating it with users (both human and machine). These users are assigned specific Policies that dictate their access patterns to different wallets and on-chain functions.Crucially, the organization’s highest security threshold, the Root Quorum,
is secured. To prevent a single point of failure, we recommend raising the root quorum to require multiple root users to approve the
most sensitive organizational changes, ensuring operational continuity even in the event of credential loss.
Contract deployment
Deployment is strictly permissioned. A designated ‘deployer’ user must have a policy that explicitly grants them permission to sign the
deployment transaction for a specific wallet and network.
Code-driven interactions
Once deployed, interactions like minting new token supply are governed by precise policies.For example, a policy can be configured to:
- Allow a ‘token owner’ user to sign a transaction
- Require the transaction to originate from a specific wallet
- Target the deployed contract’s exact address
- Call a specific function (e.g.,
mint)
Contract upgrades
Upgrading a contract is one of the most sensitive operations, as it redirects the underlying implementation logic – a process that can be exploited if unsecured.Turnkey ensures this process is secure:
- The contract is designed to be upgradeable from the start (e.g., using a proxy pattern).
- A specific ‘upgrade owner’ wallet is designated.
- A temporary, highly restrictive policy is created only when an upgrade is needed. This policy grants an ‘upgrade owner’ permission to sign the upgrade transaction.
- Once the upgrade is complete, the policy is removed, and the wallet remains dormant and secured until the next required upgrade, minimizing the window of risk.
This process is further explored in our GitHub ‘Smart Contract Management’ demo