Prerequisites
Make sure you have set up your primary Turnkey organization with at least one API user that can programmatically initiate email auth on behalf of suborgs. Check out our Quickstart guide if you need help getting started. To allow an API user to initiate email auth, you’ll need the following policy in your main organization:Helper packages
- We have released open-source code to create target encryption keys, decrypt auth credentials, and sign Turnkey activities. We’ve deployed this as a static HTML page hosted on
auth.turnkey.commeant to be embedded as an iframe element (see the code here). This ensures the auth credentials are encrypted to keys that your organization doesn’t have access to (because they live in the iframe, on a separate domain) - We have also built a package to help you insert this iframe and interact with it in the context of email auth:
@turnkey/iframe-stamper
Email Auth step-by-step
Here’s a diagram summarizing the email auth flow step-by-step (direct link):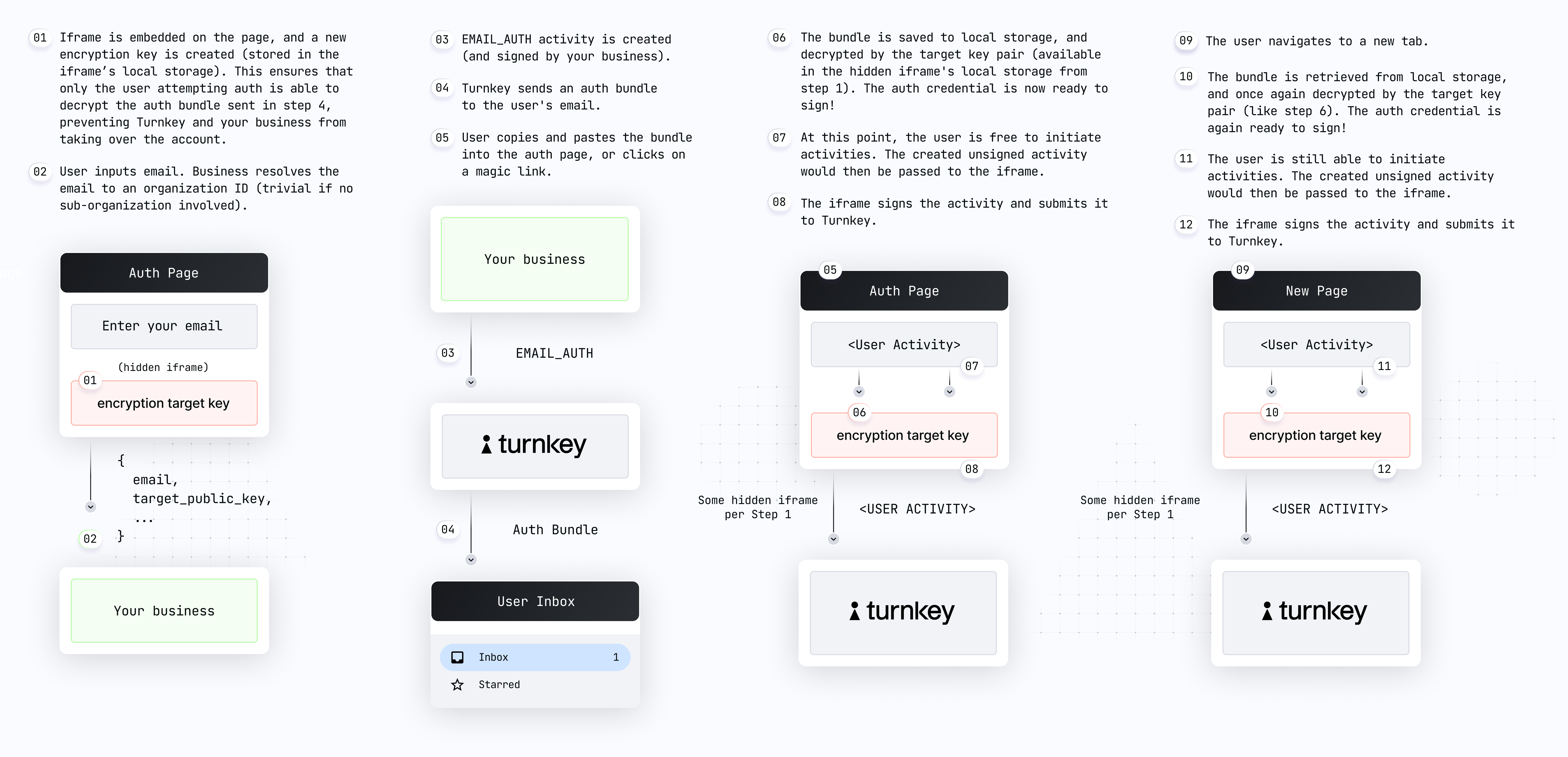
User on
yoursite.xyz clicks “auth”, and a new auth UI is shown. We recommend this auth UI be a new hosted page of your site or application, which contains language explaining to the user what steps they will need to take next to successfully authenticate. While the UI is in a loading state your frontend uses @turnkey/iframe-stamper to insert a new iframe element:Your code receives the iframe public key and shows the auth form, and the user enters their email address.
Your app can now create and sign a new
EMAIL_AUTH activity with the user email and the iframe public key in the parameters. Optional arguments include a custom name for the API key, and a specific duration (denoted in seconds) for it. Note: you’ll need to retrieve the sub-organization ID based on the user email.User copies and pastes their auth code into your app. Remember: this code is an encrypted credential which can only be decrypted within the iframe. In order to enable persistent sessions, save the auth code in local storage:See Email Customization below to use a magic link instead of a one time code.
Your app should use
@turnkey/iframe-stamper to sign a new activity, e.g. CREATE_WALLET:Because the code was also saved in local storage (step 6), it can be injected into the iframe across different tabs, resulting in a persistent session. See our Demo Embedded Wallet for a sample implementation, specifically dealing with sharing the iframeStamper across components.
Integration notes
Email customization
We offer customization for the following:appName: the name of the application. This will be used in the email’s subject, e.g.Sign in to ${appName}logoUrl: a link to a PNG with a max width of 340px and max height of 124pxmagicLinkTemplate: a template for the URL to be used in the magic link button, e.g.https://dapp.xyz/%s. The auth bundle will be interpolated into the%s
Bespoke email templates
We also support custom HTML email templates for Enterprise clients. This allows you to inject arbitrary data from a JSON string containing key-value pairs. In this case, theemailCustomization variable may look like:
alice and bob can be interpolated into the email template using the key username. The use of such template variables is purely optional.
Here’s an example of a custom HTML email containing an email auth bundle:
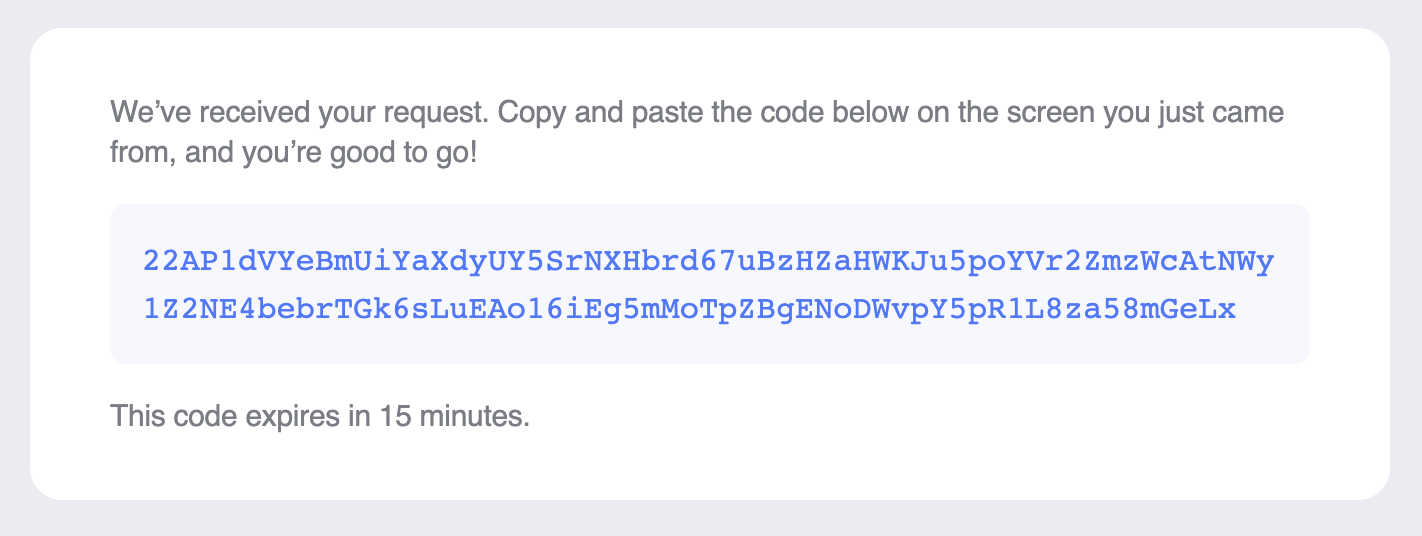
Custom email sender domain
Enterprise clients can also customize the email sender domain. To get set up, please reach out to your Turnkey rep to get started but here is what you’ll be able to configure:- Email has to be from a pre-whitelisted domain
- If there is no
send_from_email_addressor it’s invalid, the other two fields are ignored - If
send_from_email_sender_nameis absent, it defaults to “Notifications” (again, ONLY ifsend_from_email_addressis present and valid) - If
reply_to_email_addressis absent, then there is no reply-to added. If it is present, it must ALSO be from a valid, whitelisted domain, but it doesn’t have to be the same email address as thesend_from_email_addressone (though once again, this first one MUST be present, or the other two feature are ignored)
Credential validity checks
By default, if a Turnkey request is signed with an expired credential, the API will return a 401 error. If you’d like to validate an injected credential, you can specifically use thewhoami endpoint:
unable to authenticate: api key expired will be thrown.