Turnkey’s products
Turnkey covers two main use cases: embedded wallets and transaction automation.Embedded wallets
Turnkey’s embedded wallets offer the most secure way to integrate wallets into your app. With Turnkey, you can create millions of embedded wallets on behalf of your users for a flawless onboarding and in-app experience.Features
| Feature | Description |
|---|---|
| Embedded wallet kit | Speed up your integration with pre-built UI components |
| Authentication | Authenticate users via email, phone number, biometrics, social logins, etc. |
| Policies | Determine delegated access and co-ownership controls. |
| Multichain support | Sign transactions across chains with out-of-the-box support for most chains and assets. |
| Pre-generated wallets | Streamline onboarding by generating wallets for your users before authentication. |
| Sessions | Sign multiple transactions without requiring additional approvals. |
| Account abstraction | Access simple integrations for gas sponsorship and smart contract wallets. |
| Import + export | Migrate existing wallets in and out of Turnkey without exposure. |
| Delegated access | Onchain wallets with flexible co-ownership controls. |
Transaction automation
Turnkey’s transaction automation empowers teams to automate complex workflows at scale with granular policies for transaction limits, user permissions, and more.Features
| Feature | Description |
|---|---|
| Multichain Support | Sign transactions across chains with out-of-the-box support for most chains and assets. |
| Authentication | Access wallets via email, phone number, biometrics, social logins, etc. |
| API-based authentication | Create API keys with limited permissions for specific applications or use cases. |
| Compliance (audit trail) | Track events and changes across the stack, ensuring accountability. |
| Import + export | Easily migrate existing private keys without exposure. |
| Multi-signature approvals | Set a quorum of users for approving and/or denying transactions. |
Concepts
Before getting started, we highly recommend familiarizing yourself with Turnkey’s core concepts to ensure a smooth implementation. At the core of Turnkey is an important concept: instead of directly managing private keys, wallets are accessed through authenticators like passkeys, social logins, or API keys.Core terms
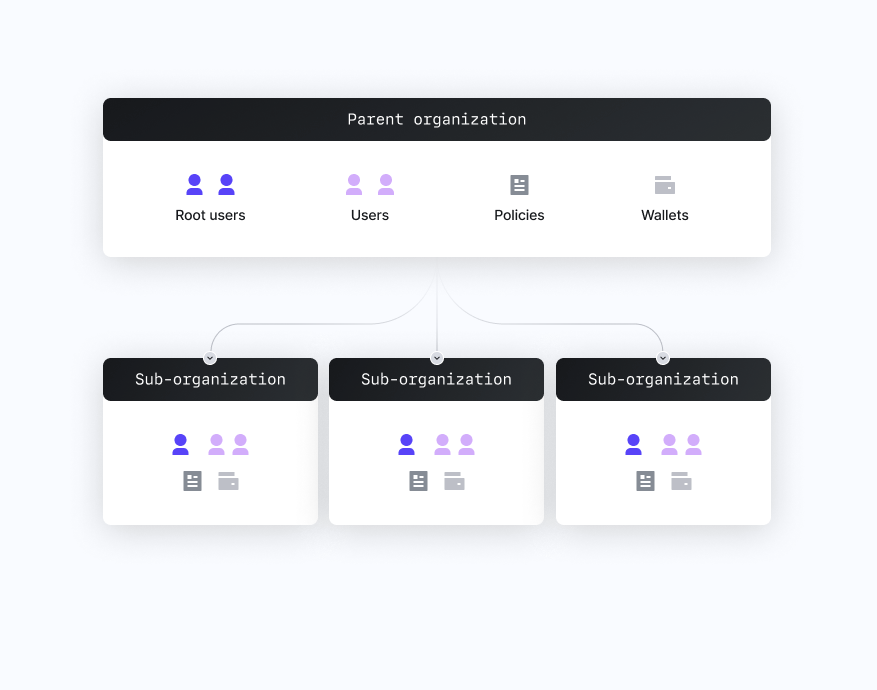
- Organizations (parent orgs): The initial parent organization typically represents an entire Turnkey-powered application.
- Sub-organizations (sub-orgs): Fully segregated organizations, typically representing an end user, nested under the parent organization. Parent orgs cannot modify the contents of a sub-org.
- Resources: All identifiers within parent orgs such as users, policies, and wallets are collectively referred to as resources.
- Users: Resources within organizations or sub-organizations that can submit activities to Turnkey via a valid credential.
- Authenticators: Each parent org, sub-org and user contain their own sets of authenticators that you can configure, including their own wallets, API keys, and private keys.
- Activities: All actions Organizations can take such as signing transactions or creating users are known as activities.
- Policies: Policies govern all activities and permissions within Organizations.
- Root users: Users with root permissions, meaning they can bypass the policy engine to take any action within that specific organization.
- Root quorum: A pre-determined consensus threshold that consists of a set of Root Users. This consensus threshold must be reached in order for any root permissions to take place.
- Wallets: A collection of cryptographic private/public key pairs that share a common seed. HD seed phrases can generate multiple wallet accounts (addresses) for signing operations.
SDKs
Turnkey provides a variety of client libraries for building with embedded wallets, transaction automation, and other common workflows. We also have several wrappers for popular web3 libraries for easy integration into existing dApps. We recommend reviewing our concepts, account setup and solution pages before moving forward with our SDKs.Embedded wallets
Transaction automation
AI-ready docs
Turnkey documentation is fully integrated with AI tooling. Whether you’re chatting with GPT, coding with Cursor, or building your own LLM assistant, our docs are structured for direct ingestion and deep context—plus, search and chat with specific pages right from your IDE or browser. Explore the docs.Security
Turnkey is the first verifiable key management system of its kind, securing millions of wallets and private keys for a wide variety of use cases. Turnkey’s security architecture ensures that raw private keys are never exposed to Turnkey, your software, or your team. We provide end-to-end private key generation and access control within secure enclaves. Our whitepaper covers our holistic security model in-depth, and speaks to our vision for building verifiable key management infrastructure. Learn more about our approach to security here.Account setup
Before diving into the code, let’s set up your organization and spin up an API keypair to unlock the full potential of Turnkey! Get started here.Support
To chat with our account team, please reach out here.For support, product feedback, and input, join our community Slack channel here.