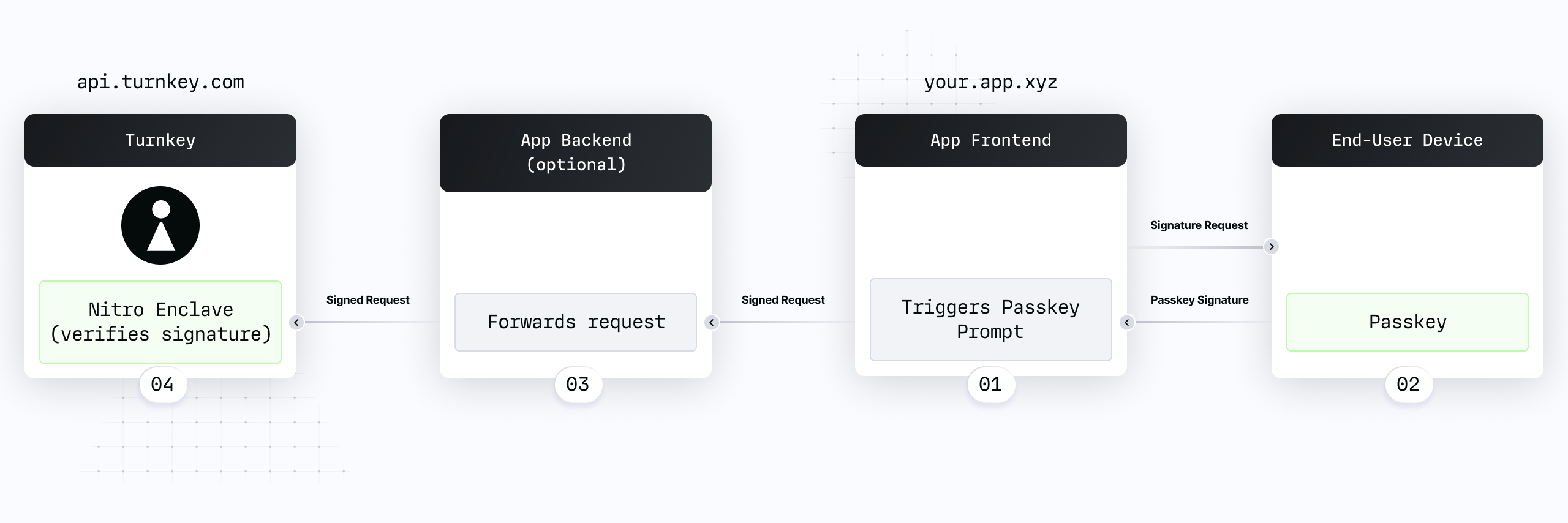
import { WebauthnStamper } from "@turnkey/webauthn-stamper";
import { TurnkeyClient, createActivityPoller } from "@turnkey/http";
const stamper = new WebauthnStamper({
rpId: "your.app.xyz",
});
// New HTTP client able to sign with passkeys
const httpClient = new TurnkeyClient(
{ baseUrl: "https://api.turnkey.com" },
stamper
);
// This will produce a signed request that can be POSTed from anywhere.
// The `signedRequest` has a URL, a POST body, and a "stamp" (HTTP header name and value)
const signedRequest = await httpClient.stampCreatePrivateKeys(...)
// Alternatively, you can POST directly from your frontend.
// Our HTTP client will use the webauthn stamper and the configured baseUrl automatically!
const activityPoller = createActivityPoller({
client: client,
requestFn: client.createPrivateKeys,
});
// Contains the activity result; no backend proxy needed!
const completedActivity = await activityPoller({
type: "ACTIVITY_TYPE_CREATE_PRIVATE_KEYS_V2",
// (omitting the rest of this for brevity)
})